✨ 2026 Futuriom 50: Key Findings and Highlights →2026 Futuriom 50: Highlights →2026 Futuriom 50: Highlights →Explore ✨
Secure Workloads and Networks at Runtime
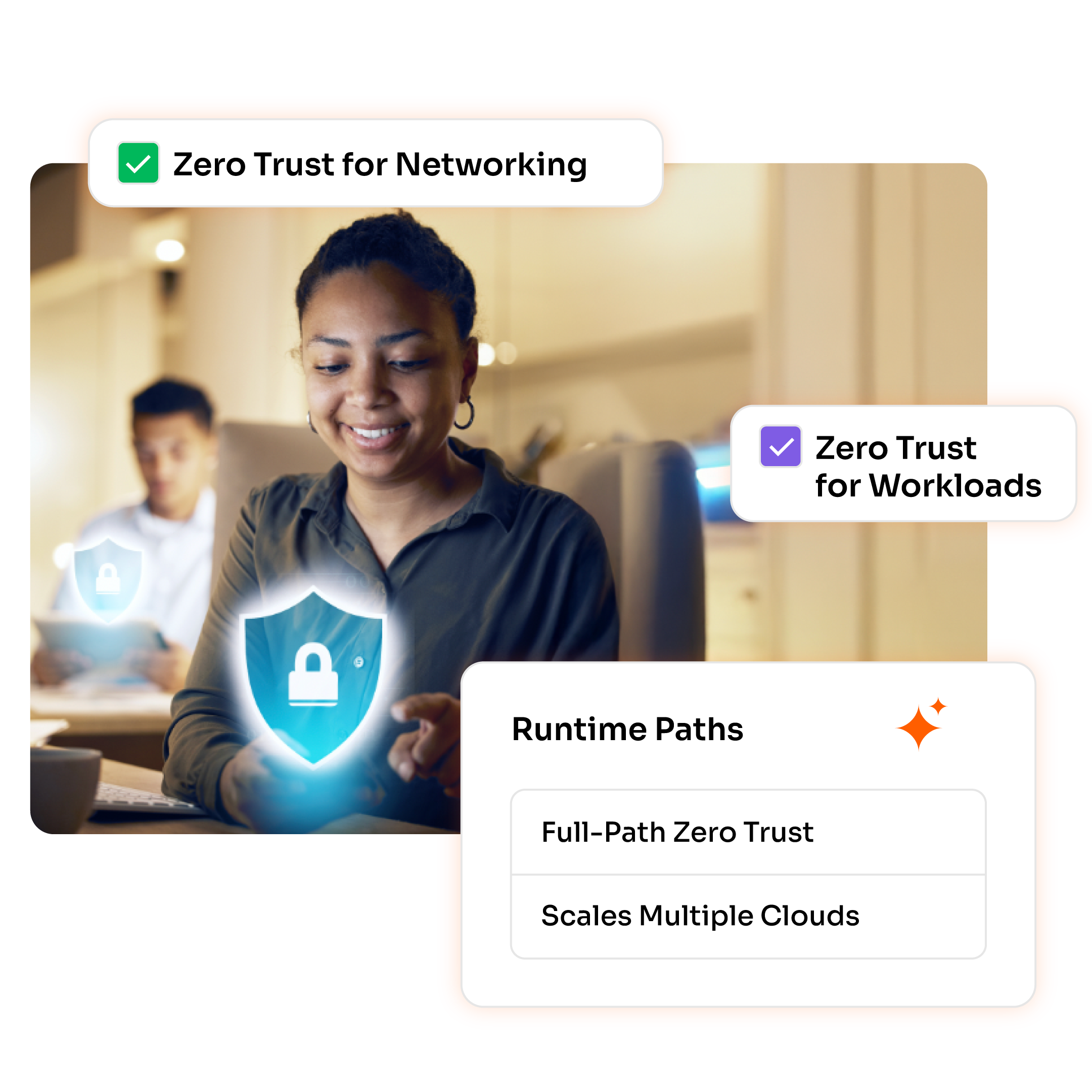
Unified, full-path zero trust that extends into the cloud and scales across multiple clouds.
Utilize the Network Layer to Enforce Zero Trust Principles
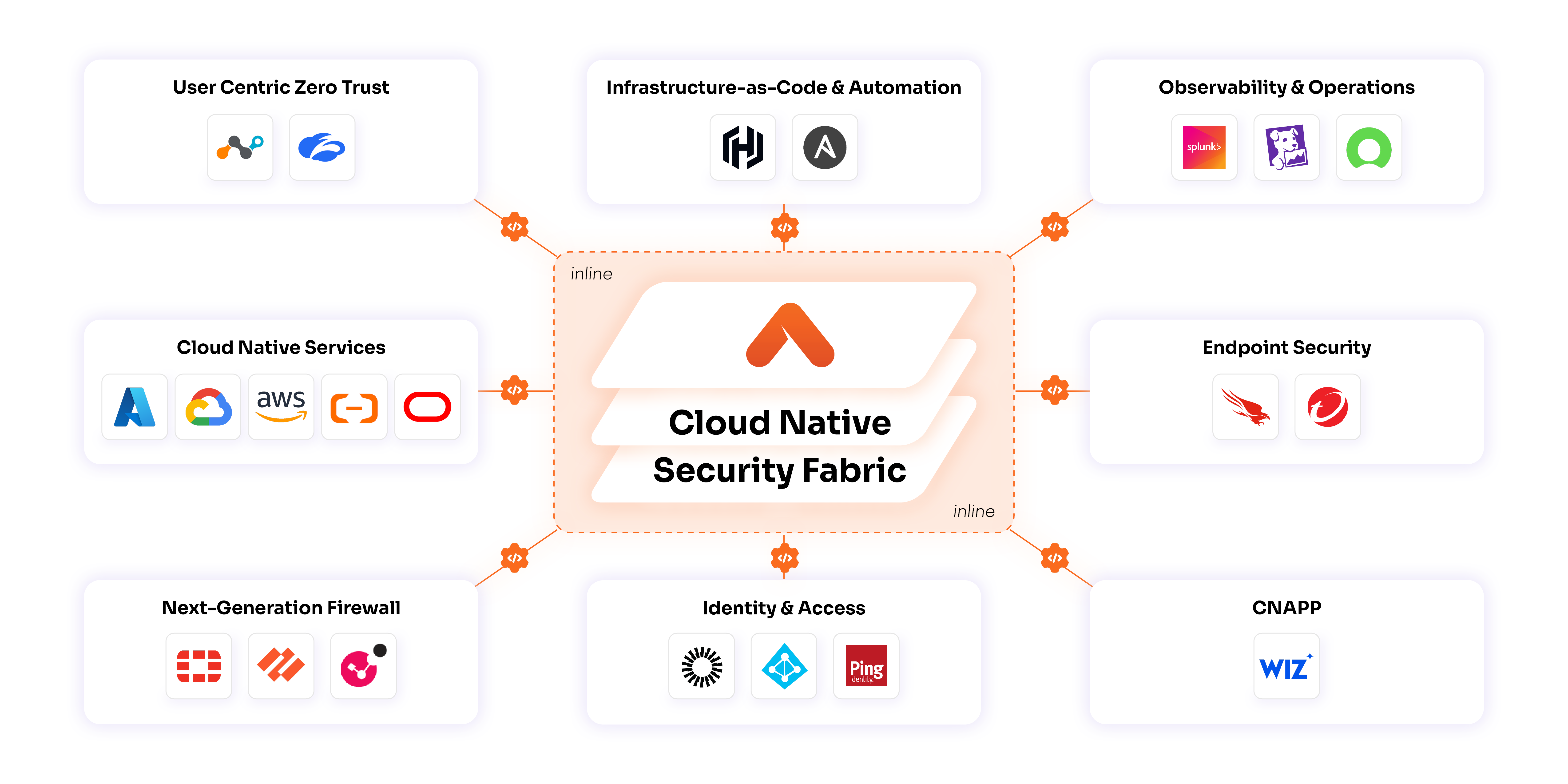
Aviatrix Cloud Native Security Fabric™ (CNSF) embeds zero trust directly into your cloud network to broker identity-aware, one-to-one workload communication and block everything else—in line, in real time, at cloud scale.
Comprised of two products—Zero Trust for Networking and Zero Trust for Workloads—Aviatrix CNSF weaves unified enforcement into the cloud fabric, encrypting every connection and securing workloads with inline protection.
CNSF delivers audit-ready compliance with HIPAA 2025, PCI DSS 4.0, DORA, NIS2, and CISA ZTMM 2.0, enabling full-path Zero Trust and operational simplicity across all clouds.

Implementing Zero Trust Across Workloads and Networks
With Aviatrix CNSF, you can define encrypted trust boundaries between networks and enforce workload-level control inside those networks. This combination of macro- and micro-segmentation enables encrypted network perimeters and runtime workload isolation.
- Zero Trust for Workloads
- Zero Trust for Networking
Zero Trust for Workloads
Secure workload-to-workload and workload-to-internet traffic in real time with inline threat prevention, egress control, and cloud-native workload protection—deployed transparently within existing cloud architectures, without network redesign or app disruption.

Zero Trust for Networking
Secure all network-to-network and cross-cloud traffic with consistent encryption, centrally orchestrated key management, and compliance-supporting telemetry across AWS, Azure, GCP, and OCI—without hardware appliances, agents, or app changes.

Built With and Trusted By World-Class Partners
Aviatrix partners with top cloud providers and technology innovators to extend CNSF, accelerate secure deployments, and drive enterprise cloud resilience.
Explore Aviatrix Zero Trust Frameworks across Workloads and Networks
Secure The Connections Between Your Clouds and Cloud Workloads
Leverage a security fabric to meet compliance and reduce cost, risk, and complexity.





