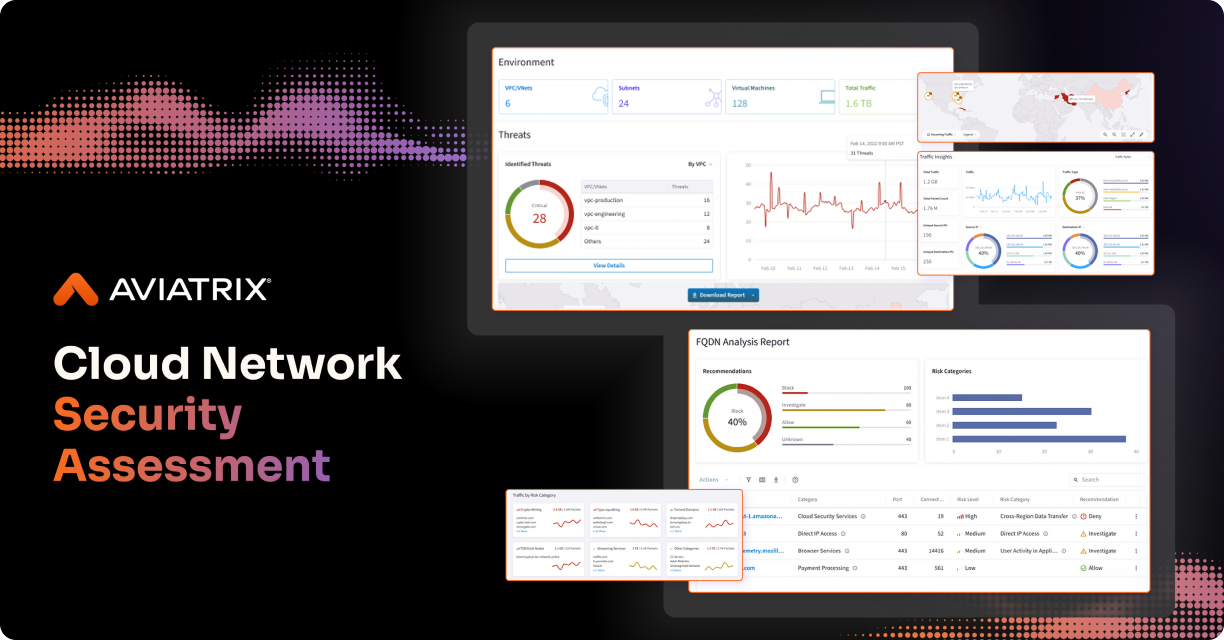
Aviatrix Workload Attack Path Assessment
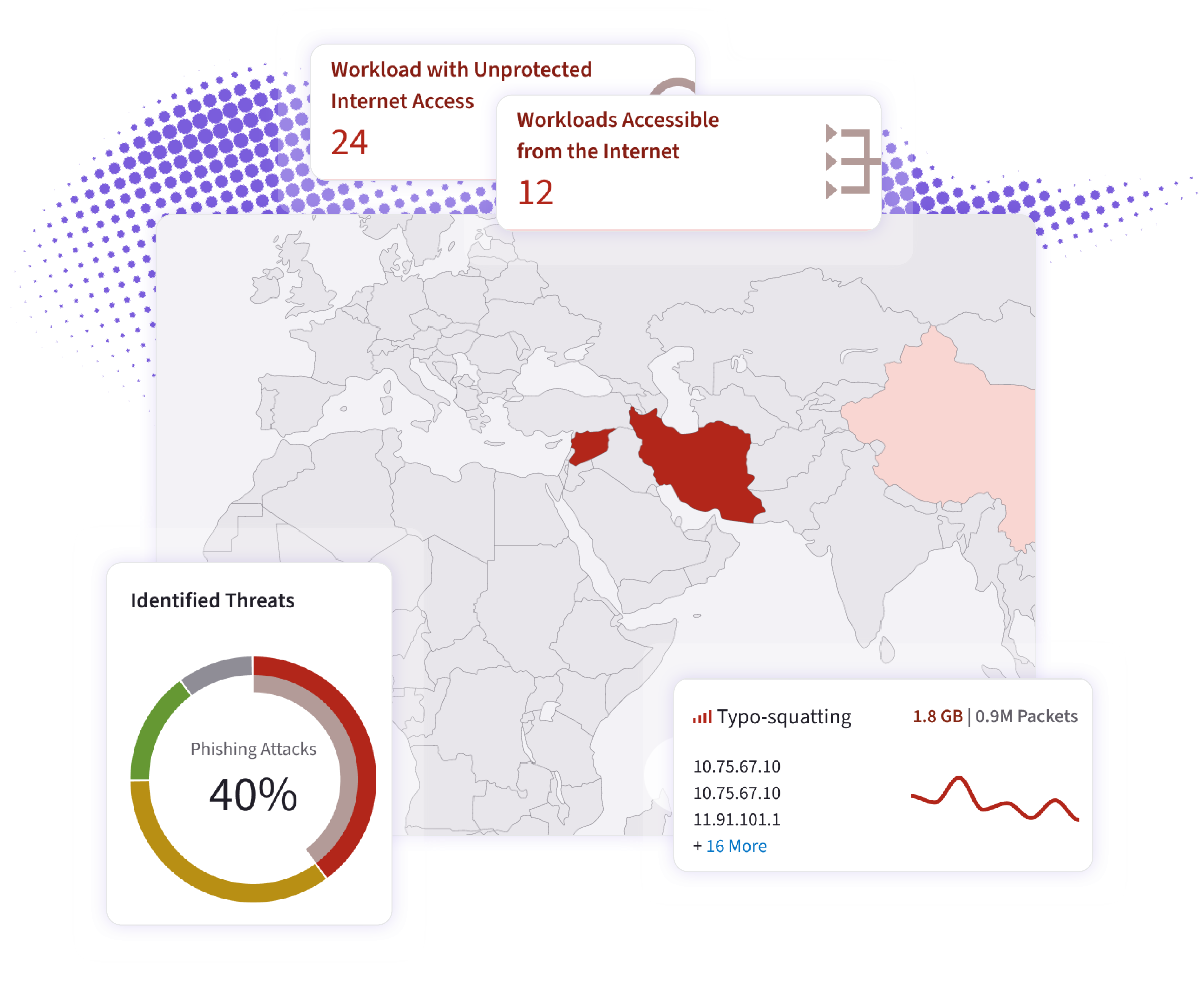
This free, agentless assessment uses AI-assisted correlation to transform flow and DNS telemetry into actionable runtime insight. It identifies patterns like DNS tunnelling, lateral movement, and suspicious egress and connects them into “Workload Breach Chains” — the multi-stage paths an attacker could realistically take through your environment.