According to Paul Pols’s Unified Kill Chain Framework, most cloud breaches involve lateral movement as attackers pivot between workloads after gaining initial access. Attackers use lateral movement because flat, unsegmented network architectures make it easy for them to explore the system and collect data before executing a massive breach. Meanwhile, data breaches are growing more expensive every year, exposing a growing reality: most tools monitor posture or perimeter (north-south traffic)— not what’s happening between workloads (east-west traffic) at runtime.
CISOs, cloud security architects, SecOps, and every other cloud network security professionals know about the problem but lack the right tools to solve it. SecOps teams need a solution that provides pervasive, multicloud network security that covers the security gaps between workloads.
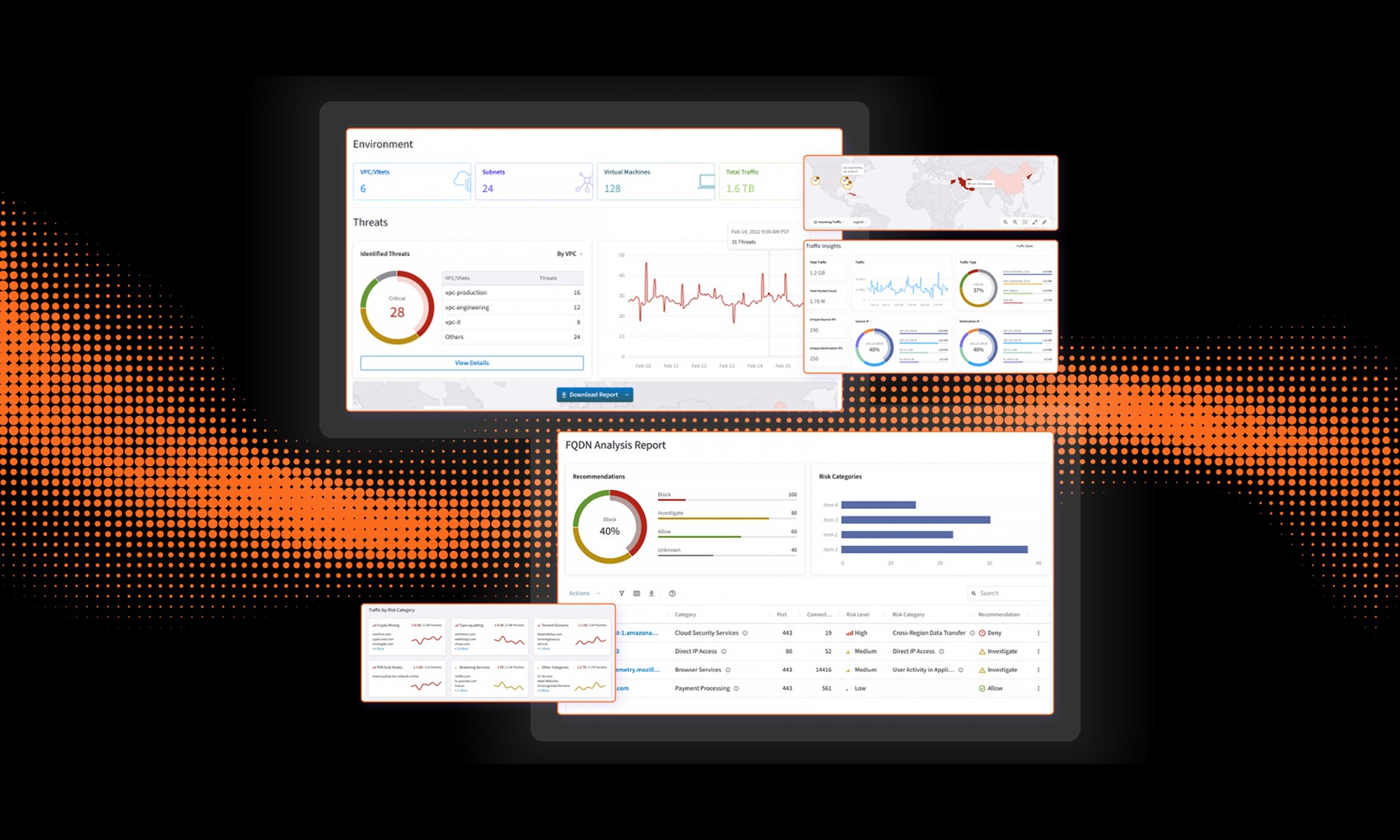
To address this workload-to-workload security gap, Aviatrix is launching a Workload Attack Path Assessment — a free, read-only analysis that gives organizations visibility into east-west traffic risks using AI-assisted correlation to transform flow and DNS telemetry into actionable runtime insight.
Without agents or re-architecture, the assessment analyzes existing flow and DNS telemetry and surfaces clear, prioritized insights into how threats could move through your environment at runtime. Learn why this assessment provides the clarity and actionable intelligence you need to close the security gaps in your network.
Why Now: Runtime Risk Is the New Blind Spot
Current solutions like CSPM (cloud security posture management), CNAPP (cloud-native application protection platform), or CWPP (cloud workload protection platform) provide a certain amount of network security protection, but they leave visibility and security gaps where attackers can hide.
Cloud tools tell you what should be happening. This assessment shows what’s actually happening, giving you the visibility you need to stop breaches before they spread — and prove zero trust is working in practice.
What the Free Assessment Surfaces
The Aviatrix Workload Attack Path Assessment helps organizations finally see their cloud the way an attacker does. The Aviatrix Workload Attack Path Assessment connects to AWS and Azure environments via read-only API access, analyzing native flow logs to surface actionable insight with zero friction. Findings include:
Telemetry Ingestion – Ingests AWS or Azure flow logs and DNS telemetry (one cloud per assessment). Normalizes and enriches data with context such as geo and threat indicators.
Behavior Detection – Identifies patterns like DNS beaconing, lateral movement, suspicious egress, and unencrypted flows.
Workload Breach Chain Correlation – Connects detected behaviors into Workload Breach Chains—showing how one action enables the next, mirroring real-world attacker behavior.
Visualization and Prioritization – Interactive dashboard surfaces findings by category and severity, with prioritized recommendations for segmentation or egress policy improvement.
Path to Enforcement – Findings feed directly into Aviatrix Zero Trust for Workloads to guide enforcement and ongoing runtime protection.
How Aviatrix Is Different
Unlike posture-based tools that only check configurations, Aviatrix assesses real runtime behavior without agents, sensors, or write access. It is:
Runtime-Focused — Detects active traffic violations, not just policy gaps
Agentless & Frictionless — Zero deployment impact
Multicloud Native — Supports AWS and Azure today
CNSF-Powered — Leverages Aviatrix’s Cloud Native Security Fabric for identity-based segmentation and runtime enforcement
Action-Oriented — Surfaces real risks, not just hygiene checklists
Built on Aviatrix Cloud Native Security Fabric (CNSF)
The assessment is powered by Aviatrix CNSF — a secure networking platform that brings runtime visibility, identity-based segmentation, and Zero Trust enforcement to cloud workloads. With CNSF, enterprises can:
Expose cloud runtime blind spots. Identify unseen lateral communication and egress routes that could enable attacker movement.
Validate zero trust effectiveness. Confirm whether segmentation and egress policies would have contained a real breach.
Prioritize control improvement. Focus remediation on high-impact areas that would break multiple potential attack paths.
Strengthen cross-team visibility. Align security and platform teams around shared runtime evidence, not static posture data.
The assessment is just the beginning. CNSF enables full-path threat prevention, automated policy enforcement, and audit-ready controls.
Get Started
The Aviatrix Workload Attack Path Assessment is available now — completely free, with no deployment, no write access, and no friction. Start your assessment today.
Check out the recently-released Aviatrix Zero Trust for Workloads, which turns zero trust principles into action.
Join us at Microsoft Ignite!
Learn more about how Aviatrix is unlocking the future of AI with insights, networking, and innovation. Join us at the Microsoft Ignite conference from November 18-21, 2025, booth 5516!