What’s Involved | What’s Your Obligation |
|---|---|
|
|
✨ Introducing Threat Research Center — Structured Cloud Breach Insights →Threat Research Center →Threat Research Center →Explore ✨
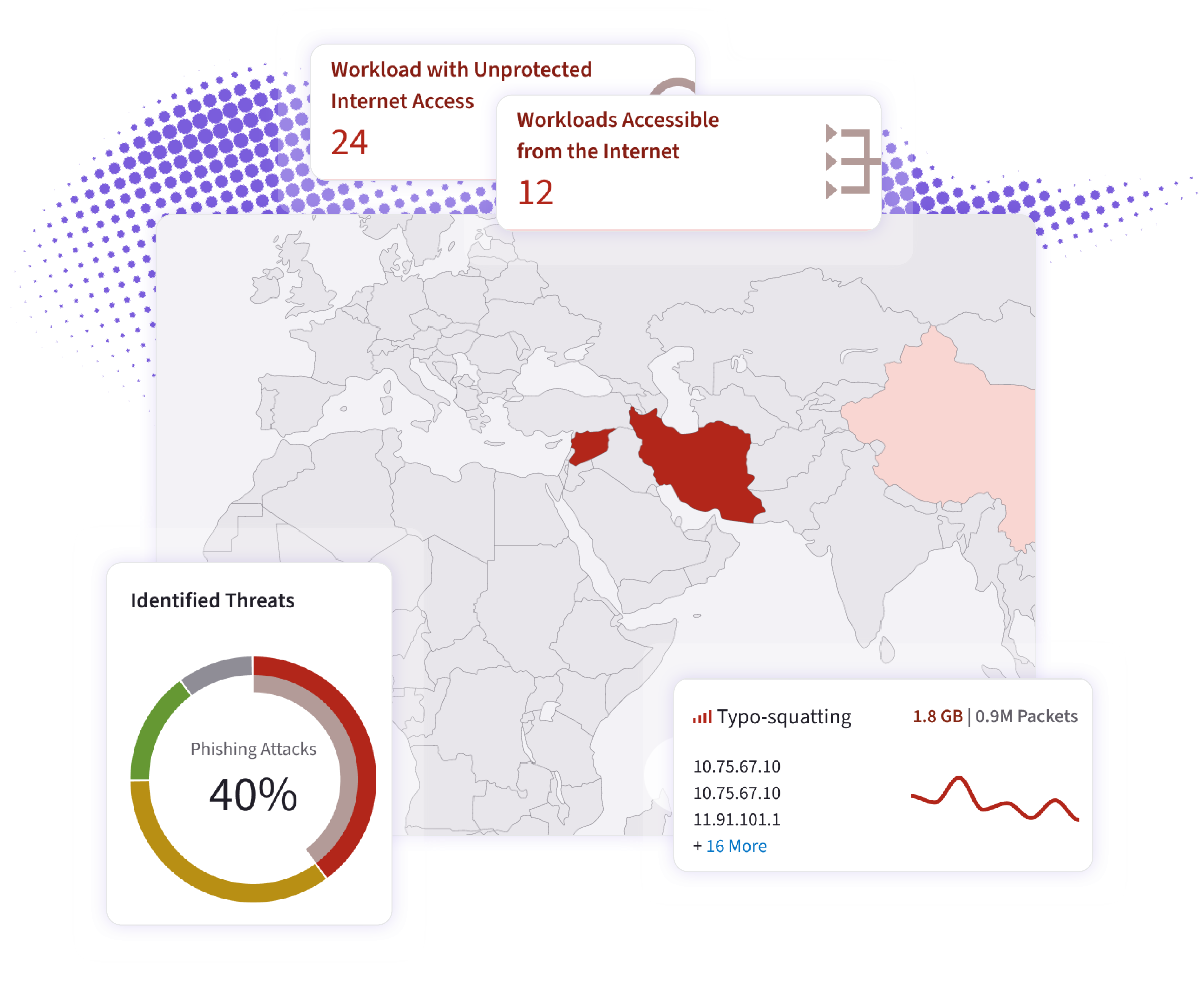
Lateral movement between trust zones.
Outbound traffic to TOR/malicious IPs.
Runtime policy drift vs Zero Trust segmentation intent.
of breaches are detected in the first hour (IBM)
of breaches involve lateral movement (IBM)
average time for attackers to move laterally inside a network after initial breach (CrowdStrike)
What’s Involved | What’s Your Obligation |
|---|---|
|
|
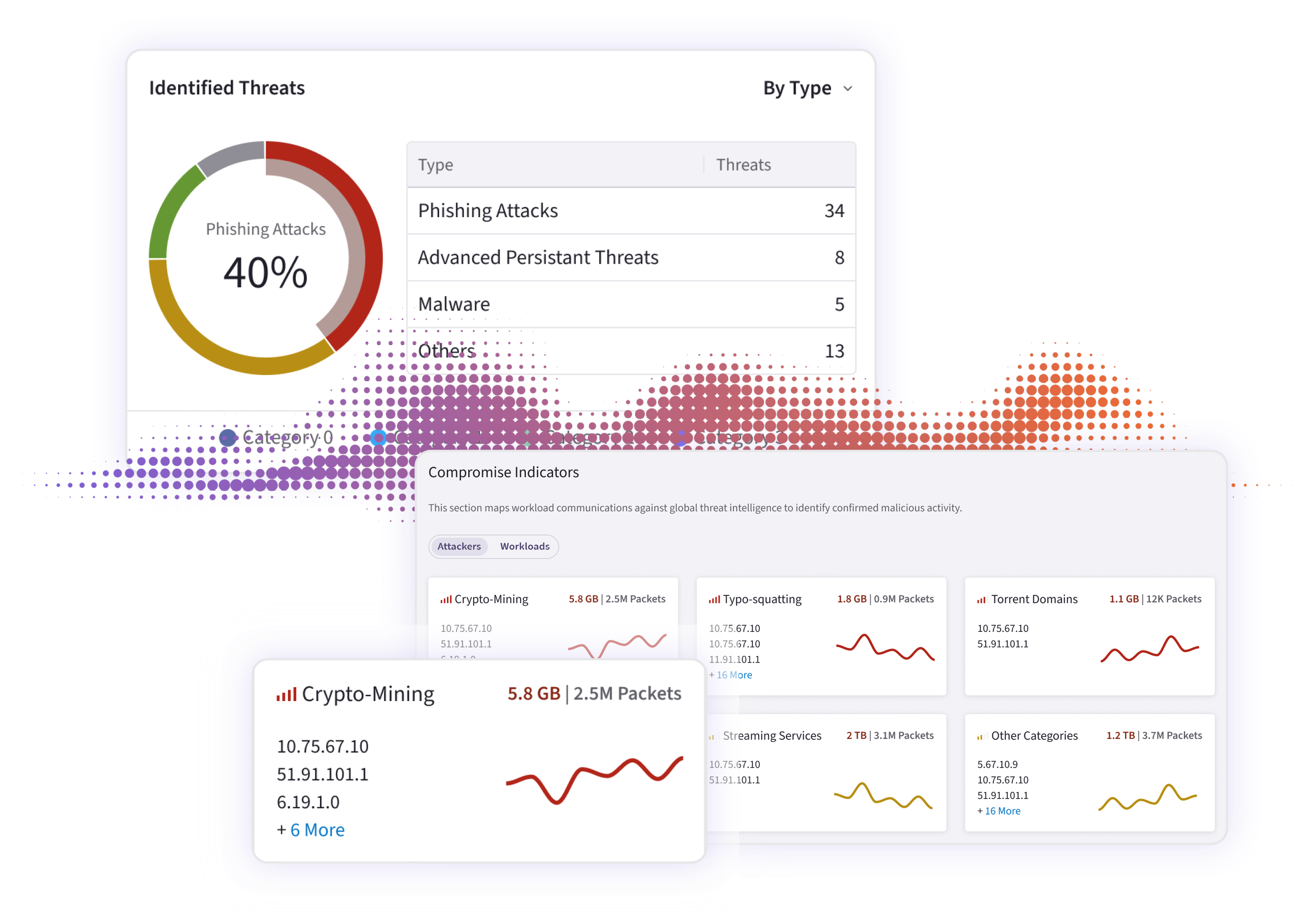
Discover lateral movement paths, segmentation breakdowns, and uncontrolled egress flows — all mapped to real workload behavior in minutes.
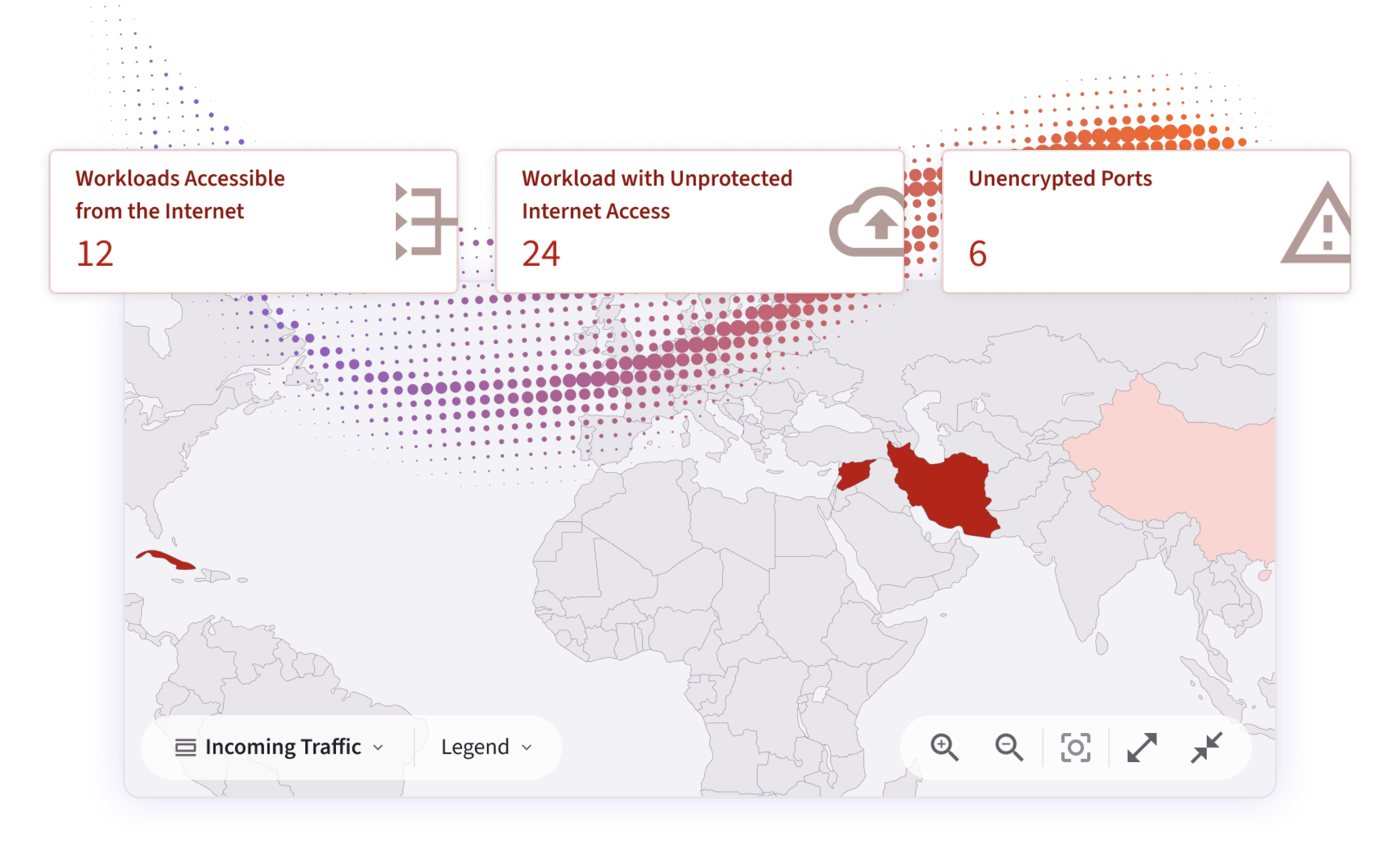
Get a real-time view of egress behavior — from TOR traffic to foreign IPs — and a roadmap to eliminate high-risk outbound paths across cloud networks. Because outbound traffic is often the final stage of a breach—command-and-control, data exfiltration, or backdoor persistence—you need to see it before attackers succeed.



















Aviatrix eliminates runtime blind spots by analyzing real workload traffic — delivering Zero Trust insights posture tools miss, without agents or friction.

