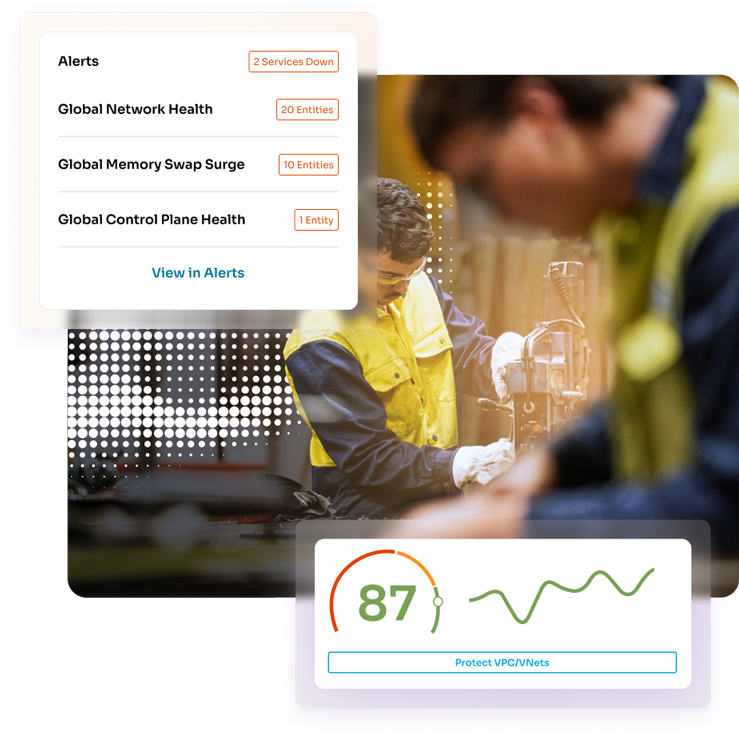
The Solution: Aviatrix Zero Trust for Networking
Enable fabric-wide, software-defined encryption and policy visibility across every VPC, VNet, and region. Aviatrix Zero Trust for Networking—part of the Aviatrix Cloud Native Security Fabric™—delivers consistent encryption, centralized key orchestration, and compliance-ready telemetry across all clouds without hardware or re-architecture.