Secure Networks and Runtime Paths
Unified, full-path zero trust that extends into the cloud and scales across multiple clouds.


Dual-Layer Zero Trust
With Aviatrix, you can define encrypted trust boundaries between networks and enforce workload-level control inside those networks. This combination of macro- and micro-segmentation enables encrypted network perimeters and runtime workload isolation.
- Networking
- Workloads
Zero Trust for Networking
Secure all network-to-network and cross-cloud traffic with consistent encryption, centrally orchestrated key management, and compliance-supporting telemetry across AWS, Azure, GCP, and OCI—without hardware appliances, agents, or app changes.
Zero Trust for Workloads
Secure workload-to-workload and workload-to-internet traffic in real time with inline threat prevention, egress control, and cloud-native workload protection—deployed transparently within existing cloud architectures, without network redesign or app disruption.
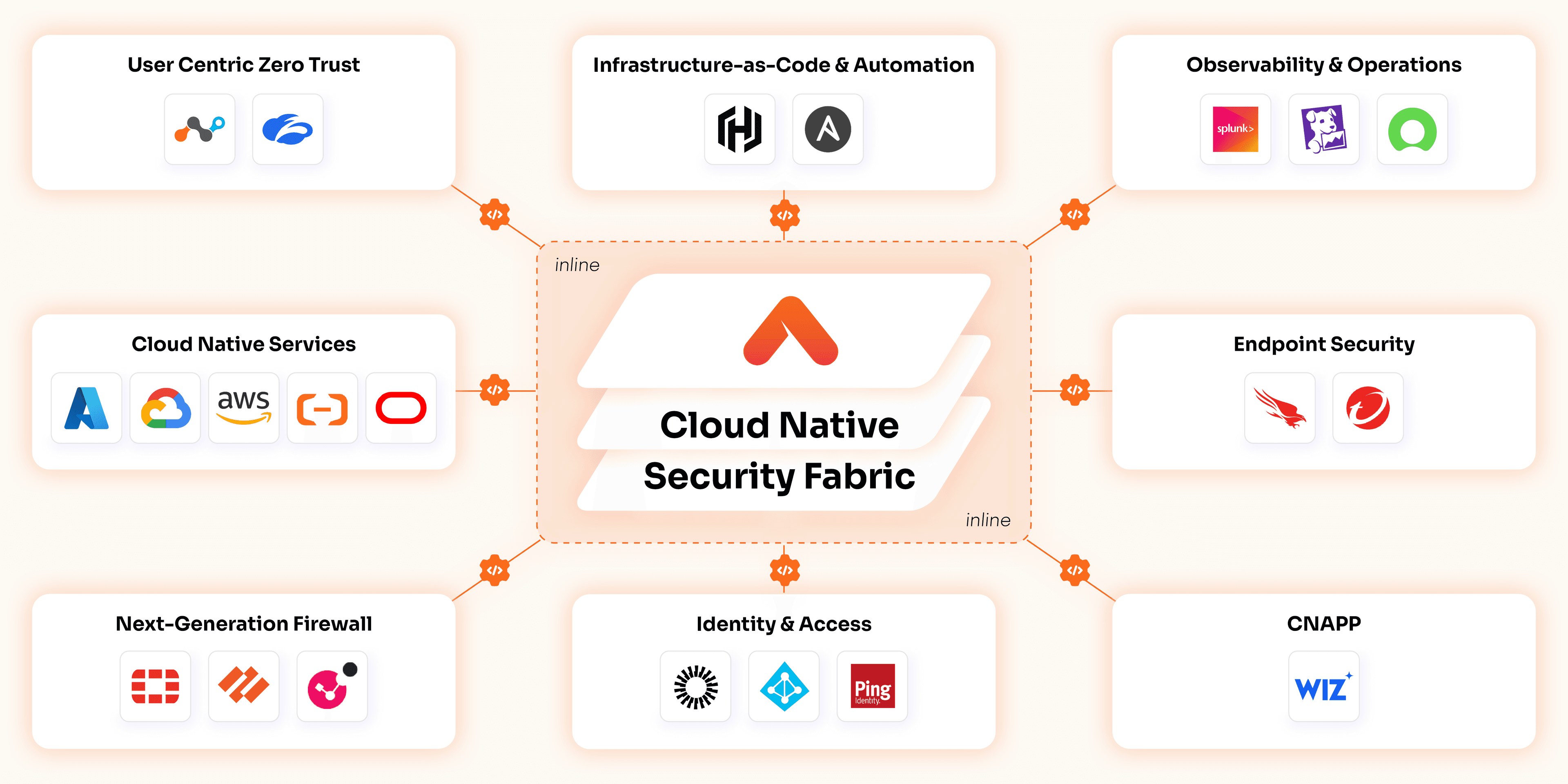
Built With and Trusted By World-Class Partners
Aviatrix partners with top cloud providers and technology innovators to extend CNSF, accelerate secure deployments, and drive enterprise cloud resilience.

Learn More About Full-Path Zero Trust
Secure The Connections Between Your Clouds and Cloud Workloads
Leverage a security fabric to meet compliance and reduce cost, risk, and complexity.







